the case against Public VPN providers
I will try to make my case in several parts, going through claims made by Public VPN (I will continue just calling them VPN providers, I know private VPN do something else, for the sake of readability) providers and why they are either bullshit or outright malicious.
Chapter 1: the people
Running a VPN, especially one that truly does not log anything, takes a special kind of person. Running a VPN is incredibly profitable, and I will get to the math later, however it exposes you to whatever your users are doing using that service. That includes not just torrenting, but child porn, ransomware and any other criminal activity done on the internet. A VPN provider has to get reports of drug deals, raped and filmed children or hospitals with locked data due to a ransomware attack, and knowing they are the only clue investigators have, answer "nah, we don't log anything, bad luck". Everyone has to understand what they will be dealing with, and either the no logging policy is a lie, or they have to prefer profit to any sort of justice.
You may read this as an uninteresting critique, one that has been repeated many times, but I urge you to look at it from the point of whom you trust with your internet connection, someone who has to prefer profit despite being involved with some of the most heinous crimes imaginable to, you know, decency.
Your data is protected, because it is currently profitable to protect it, not because someone is inheretnly a good person.
Chapter 2: the profitability
So how profitable is it to run a VPN? there surely must be tons of cost......
the usual pricing of VPNs is between $2-$8 a month, so how much can be done with that amount of money? well the cheapest VPS I could find, which would be a server that can handle at least one VPN connection, is priced at $1.23 a month. Maybe more reasonable would be if I went to Hetzner and get their smallest offering, at around €3.49. That will get you a host that can handle at least 5 concurrent users at reasonable speeds. Even if we assume you are maxing out your internet connection 8h a day, a single one of these approx. $4.04 server can handle some 15 users, if they are distributed globally, that pay on average $5 a month. So 6% of their income would go to pay for infrastructure.
"but VPN providers have to develop...." Shut the fuck up. They repackage wireshark or OpenVPN. All they have to do is make a website and some user managemement. This is one of the reasons why they try to pivot into security, which I will get into in detail.
Chapter 3: How does basic internet browsing work?
At first you will go to your browser and put your banks URL into your browser. Let's say that is https://acme-bank.com/my-account. Your browser will take the URL, extract the domain, and start digging in DNS to try to find where it is. Usually you will be using your ISP's DNS, so you will essentially ask your ISP, over an unencrypted protocol, what is the IP address for acme.bank.com. You will receive a DNS response and start connectign to it. You do not actually connect there using HTTP, since you are using that S at the end, as virtually all banks require today. That connection, upon establishing, will first get the destination certificate and check the certificate chain up to the root certificate, to check that the certificate is valid. There are only a few trusted root certificate authorities in the world, and you can only get a certificate for a website for one of them, if you do really own the domain. Your browser also checks the destination domain against the target certificate, to make sure it matches. The communication between you and your banks web server is established via TLS, which is asynchronous encryption - you both have certificate pairs, private and public one, and you can use the public one to encrypt data and they can only be unencrypted with the private one from the same pair. This establishes a tunnel, today most commonly you will see Elyptic curve encryption with 256 bit key lenght -> that is very reasonably strong.
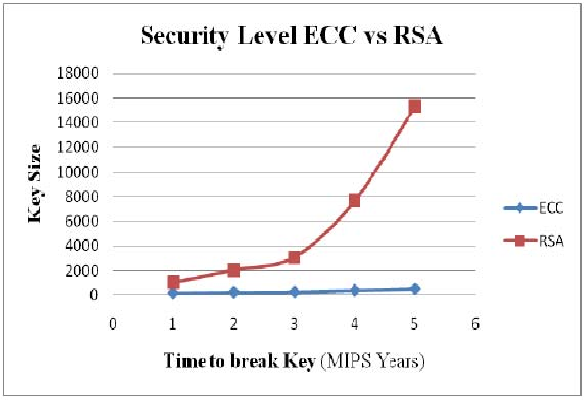
to break a session like that, if you collected the information on the way, would mean some 1.83 times 10^57 years if you had 10PFLOPS of computing power available, or some 100 high end GPUs. The age of the universe is a mere 1.38 times 10^10 years. And that is the encryption built into virtually every one of your website visits as is.
After that you will establish the actual HTTP connection which runs inside of the TLS tunnel. Now your bank or your email provider will serve you content. They will know who you are because you log in, and in case of your email provider, they will happily tell everyone, usually over cookies, like the google tracking stuff or the facebook pixel.
Essentially there are several things that your host tells on you when you connect to a website.
- your IP address
- your user agent (read as version of your browser and OS)
- your persistent cookies (meta pixel/ google analytics and many more)
- the window size your browser runs in
- your language
- day/night mode enablement and some more stuff like timezone sometimes even location according to built in GPS in your host.
Your ISP can track
- your DNS requests
- your connections (source/destination only)
The website can track
- your IP address
- your identity from cookies
- your metadata like display size etc.
- your physical location according to built-in GPS
An IP address btw. is not a reliable identificator for 3rd parties, if you connect from a coffee shop, you will have the same public IP address as every other person in the same coffee shop, airports may have a range of addresses, but it would still be 256 addresses for every person in the airport, therefore no one site would actually use IP addresses to track users, it would be useless.
But, do ISPs log the data they can collect?
and I have not found it there. (this screenshot is a short example, I have delved deeper into the financials, at least for the financials in 2022) Eventhough this conclusion cannot be guaranteed, at least we can look at the institutions that would want to have access to it, like BIS, who's whole budget in 2017 was 1.65 billion crowns, even if it grew 3 times, they couldn't possibly fit in data from just one ISP.
The Claims
VPN providers rarely make outlandish claims on their website, they let online influencers make them. Plausible deniability I guess.
"Secured with an encrypted tunnel that noone can get into! including hackers and governments!"
What this ignores is where the attack surface of a typical individual really is. This makes it seem like you can't be tracked or hacked, but doesn't say that outright, because it would be a lie. Let me first explain what happens (today) when you let's say access your bank or email accounts.